How does EnforceCloudPasswordPolicyForPasswordSyncedUsers policy works?
If you have an expiration policy configured in your on-premise environment, this is not synced to Azure AD. This results in the scenario where a user can continue to work and access company resources when authenticating against Azure AD, although the password has expired in the on-premise AD. If you want to be able to have the moment of expiration of both passwords in sync, you should consider implementing this feature.
Why should I use the EnforceCloudPasswordPolicyForPasswordSyncedUsers feature?
Many organizations who are using password hash synchronization and syncing their identities from AD to Azure AD are not aware of the consequences of an expired password. The expiration policy within Azure AD should comply with your on-premise AD, therefore you need to configure the EnforceCloudPasswordPolicyForPasswordSyncedUsers feature before it would mark a password as expired
How to enable EnforceCloudPasswordPolicyForPasswordSyncedUsers feature?
Below you will find step-by-step guidance on how to enable and configure this feature.
- Run the below Powershell command to check if the feature is enabled:
Get-MsolDirSyncFeatures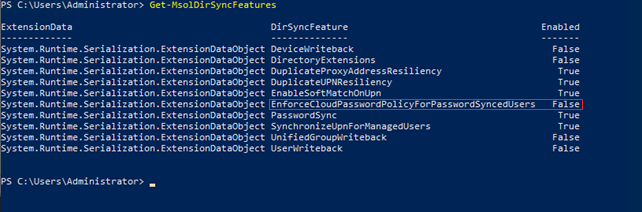
- To enable the EnforceCloudPasswordPolicyForPasswordSyncedUsers, run the below command in your tenant:
Set-MsolDirSyncFeature -feature EnforceCloudPasswordPolicyForPasswordSyncedUsers $trueBy default, the value DisablePasswordExpiration is set for every synced user, which means that the password expiration does not comply with the on-premise AD policy. This results in the scenario that a user won’t be prompted to change the password when they try to access company resources.
- Run the below command to check which user has a password expiration set:
Get-AzureADUser | Select-Object UserPrincipalName,passwordpolicies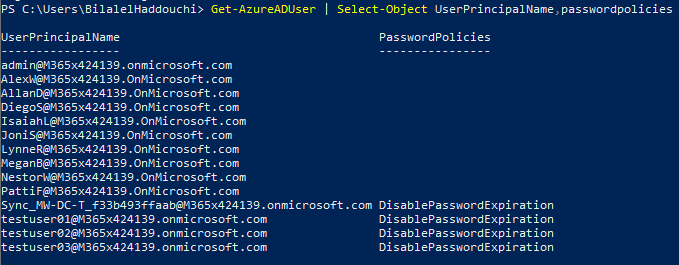
When you want to comply with the on-premise password expiration policy, the PasswordPolicies value should be set to None. To get this done, you should change the on-premise password of a user and start initial sync. After the sync, the value should change to “None”.
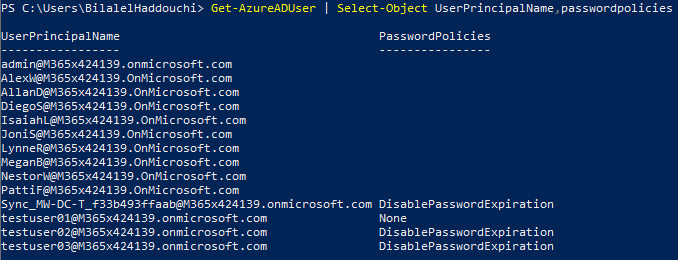
- Run the below command to change the value manually to “None” for a specific user:
Set-AzureADUser -ObjectID YourUserName -PasswordPolicies NoneImportant note:
If you have specific synchronized AD accounts, e.g. Service Accounts that need to have non-expiring passwords in Azure AD, you must explicitly add the DisablePasswordExpiration value to the PasswordPolicies attribute.
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

