Turn on auditing to monitor account attacks
There is no doubt that all of the new security features in the modern versions of Windows will help keep your computer more secure. However, these features become less valuable when they are not turned on by default. One feature, known as user account auditing, is not turned on by default. With this feature is turned off, anyone with physical access or remote access to through a hole in your firewall (such an opening for Remote Desktop) can use a brute force attack against your user account for as long as they want without getting noticed at all. How? The default audit security policy is configured to not log any account logon events, successful or failed.
This allows an attacker to try to hack your accounts for as long as it takes to break in. There are a few ways to protect against this that I am going to go over in my next article about the Account Lockout policy. But first, it is important to turn on this account auditing so that you can see who may be trying to break into your accounts. After you have adjusted the auditing security policy, you will be able to see any account attacks including the account that they tried to logon with and where the request came from.
Let’s get started and turn on audition for failed logon events:
- Click on the Start Button and key in secpol.msc in the box and hit Enter.
- Navigate through Local Policies and Audit Policy.
- Right click on Audit account logon events policy and select Properties.
- Check the Failure box and hit OK.
- Right click on Audit logon events policy and select Properties.
- Check the Failure box and hit OK. Your screen should now look like the figure below:
- Close Local Security Policy editor.
Your computer has now been configured to log all failed user account logon attempts.
Once you have turned on account auditing, you can view the logs in Event Viewer (run eventvwr.msc) under Windows Logs and Security.
Create an Account Lockout Policy
Creating an Account Lockout Policy will protect your account by limiting the number of time a remote application or attacker can try to guess your password.
This works by automatically locking out your account after a designated number of incorrect passwords were entered.
Your account will remain locked out for a designated period of time before it is automatically unlocked and it can be logged into again.
This provides a valuable addition to your account security because it can render brute force password attacks useless.
If you have your lockout threshold set to 4 bad attempts and the lockout duration to 15 minutes, an attacker can try to guess your password a maximum of 16 times per hour.
Now that you know how valuable an Account Lockout Policy is, let’s get it setup on your computer:
- Click on the Start Button and key in Secpol.msc and hit Enter.
- Navigate through Account Policies and Account Lockout Policy.
- Right click on Account lockout threshold and select Properties.
- Enter in the value you want to use and hit OK to save. I like to use 4 here.
- Windows will set the default values for the lockout duration and Reset account lockout counter values. If you want to change these values from the defaults (30 minutes), right click on them and select Properties. After making your changes hit OK to save and exit.
Change Remote Desktop RDP Port
Port 3389 is the home of the remote desktop protocol that powers Remote Desktop Services on all modern versions of Windows. If your system has Remote Desktop enabled, it is listening for connections on port 3389. Since this port is both well known and can be used to attack accounts, it is low hanging fruit for script kiddies and bots looking for an easy target.
Theoretically on a system that does not have an account lockout policy in place which by the way is not a system default, the RDP protocol can be used to get the administrator password with brute force. Brute force is a fancy way of saying trying all possible passwords. If the system never locks out the account then time is the only barrier to eventually getting you password and logging in.
The first defense is to implement a good account lockout policy but that does not solve the entire problem. Any administrator of a public facing Windows web server will notice that their server is continiously attacked by bots looking for an easy target. The bots will often lock out your accounts which can be very annoying.
To protect your system from the bots and script kiddies I always reccomend changing the default RDP port. This will not fool an intelligent attacker but it will weed out the noise.
There are two methods you can use to change the default RDP port. The first is a simple registry hack:
Open up Registry Editor by running regedit. Then navigate to HKEY_LOCAL_MACHINE, SYSTEM, CurrentControlSet, Control, Terminal Server, WinStations and RDP-Tcp. Right click on the PortNumber dword and select Modify. Change the base to Decimal and enter a new port between 1025 and 65535 that is not already in use. Finally click OK.
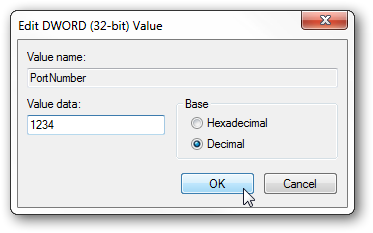
The second method uses a Microsoft Fix It wizard. Click here to download the utility from Microsoft then click next to start the wizard. On the PortNumber screen enter the new port you want to use, click next and that is it.
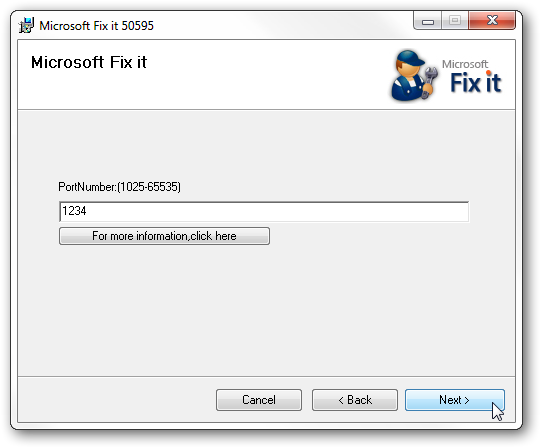
Make sure to reboot after either method to ensure the change is active.
Keep in mind that the next time you want to connect to your system with RDP you will need to provide the port number. You can do that from the Remote Desktop client by appending a colon after the host name or ip address followed by the port number. For example, if I have a computer with host name of tweak with RDP running on port 1234 I would use tweak:1234 in the remote desktop client hostname field.
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

