Introduction
So far in this article series I have spent a lot of time talking about security settings that you can configure on your wireless access points, as well as a way to configure Windows Server to authenticate wireless traffic before allowing it to reach your wired network. In this article, I want to conclude the series by talking about client-side wireless security.
Client-side wireless security involves configuring desktops and laptops (and any other wireless clients on your network) to use a specific wireless policy. In Windows Server 2008 and in Windows Server 2008 R2, wireless network policies can be managed through the Group Policy Management Editor. It is possible to manage wireless networking related group policy settings in a Windows Server 2003 environment as well, but in order to do so you will have to download a tool from Microsoft that extends the Active Directory schema to support wireless policies. Configuring Windows Server 2003 environments is beyond the scope of this article, but I wanted to at least mentioned that it is possible to use group policy settings to control wireless access in a Windows Server 2003 environment.
Before I Begin
Windows Server 2008 and Windows Server 2008 R2 make it relatively painless to create wireless policies. However, there are two things that you need to know before I show you how it’s done. First, as you have probably already figured out, the policies that I am going to show you how to create are only effective for domain members. This is because we are implementing the wireless policy through the Active Directory rather than using local security policies.
The other thing that you need to know is that there is no such thing as a one-size-fits-all wireless policy. Windows requires you to create a wireless policy for machines running Windows Vista or Windows 7. You must create a separate wireless policy for any machines that are running Windows XP.
Creating a Wireless Policy
For the purposes of this article, I want to show you how to create a Windows Vista / Windows 7 policy that acts as a part of the default domain policy. To do so, log into a domain controller as an administrator and enter the MMC command at the Run prompt. Choose the Add / Remove Snap-In command from the server’s File menu. When you do, you will see a list of available snap-ins. Choose the Group Policy Management option from the list of available snap-ins and click Add, followed by OK.
When the console opens, navigate through the console tree to Group Policy Management | Forest | Domains | <your domain> | Default Domain Policy. When you do you will see a warning message telling you that the changes that you are about to make are global. Click OK to clear the warning. Now, right click on the Default Domain Policy container, and choose the Edit command from the shortcut menu, as shown in Figure A. This will cause Windows to open the default domain policy within the Group Policy Management Editor.
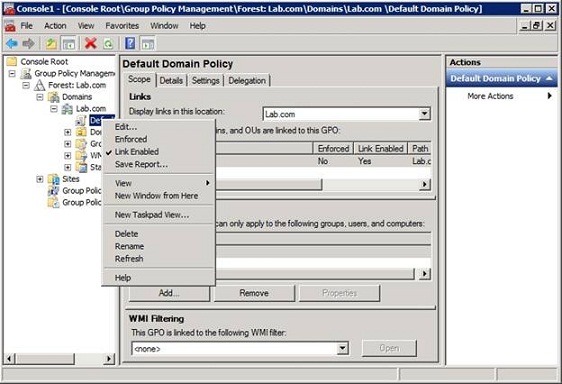
Figure A: Open the default domain policy.
When the Group Policy Management Editor opens, navigate through the console tree to Computer Configuration | Windows Settings | Security Settings | Wireless Network (IEEE 802.11) Policies, as shown in Figure B.
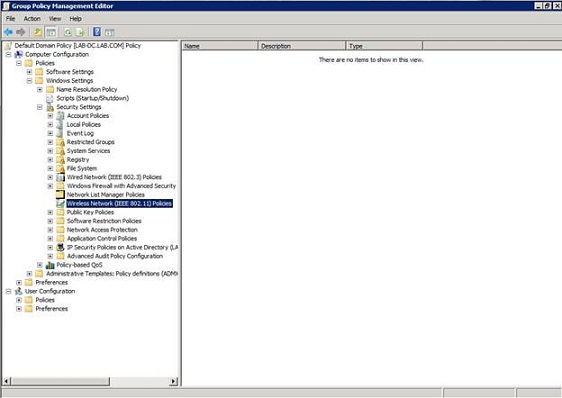
Figure B: Navigate to the Wireless Network (IEEE 802.11) Policies container.
Now, right click on the Wireless Network (IEEE 802.11) Policies container and choose the Create a New Wireless Network Policy for Windows Vista and Later Releases command from the shortcut menu. When you do, Windows will open the New Wireless Network Policy Properties sheet, as shown in Figure C.
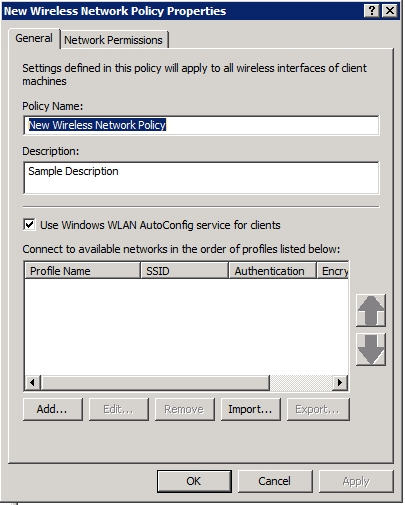
Figure C: You must use the New Wireless Network Policy Properties sheet to create a wireless policy.
As you can see in the figure above, you must assign a name to the policy that you are creating. By default, Windows uses the name New Wireless Network Policy. Personally I recommend using something a little bit less generic. There is also an area beneath the Policy Name field where you can enter a description for the policy that you are creating.
Once you have created a name and a description for your new wireless network policy, the next step is to specify the wireless networks that are members of the domain are allowed to connect to. Believe it or not, Windows allows you to specify both infrastructure and ad hoc wireless networks. To do so, simply click the Add button and then tell Windows if you want to add an infrastructure or an ad hoc network. Upon making your choice, Windows will display the New Profile Properties sheet that is shown in Figure D.
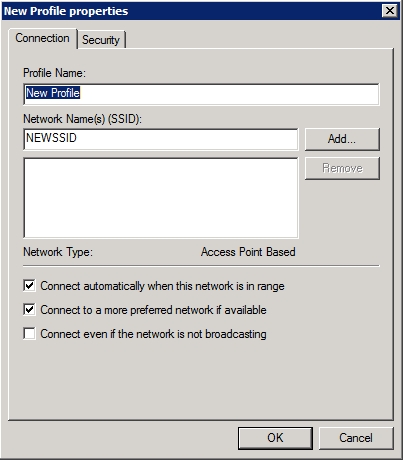
Figure D: You can create a profile for a wireless network.
As you can see in the figure, this screen allows you to provide a list of SSID’s that are associated with a particular wireless network. You will notice that at the bottom of the Connection tab there is an option to connect even if the network is not broadcasting.
This properties sheet also contains a Security tab, which you can see in Figure E. This tab lets you control the authentication and encryption methods that clients must use when connecting to the wireless network. Once you have provided the settings that are appropriate for your network, click OK to return to the New Wireless Network Policy Properties sheet.
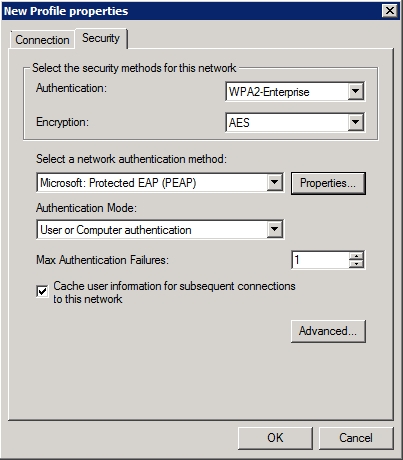
Figure E: The Security tab allows you to manage the authentication and encryption settings for a wireless network.
In addition to allowing you to add wireless network policies, the New Wireless Network Policy Properties sheet contains a Network Permissions tab, which allows you to manage some general security settings related to wireless networking.
As you can see in Figure F, this tab gives you the option of blocking access to either ad-hoc or to infrastructure networks. More importantly however, you have the ability to block users from connecting to specific wireless networks. To do so, click the Add button, specify the network’s SSID, and then set the permission to Deny, as shown in Figure G.
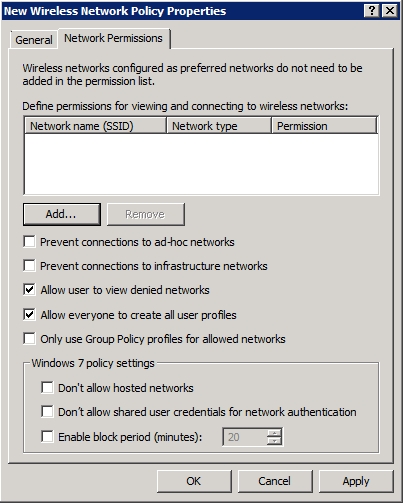
Figure F: You can block access to ad hoc or to infrastructure networks.
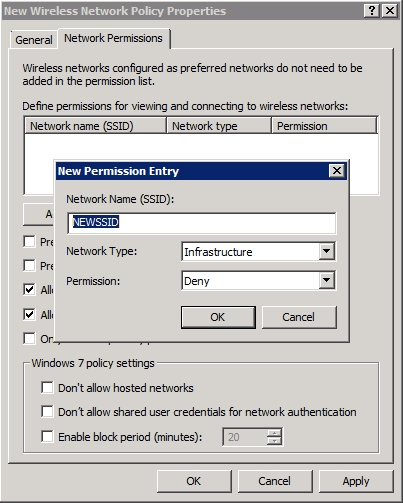
Figure G: You can block access to specific wireless networks.
In a situation like this in which the wireless policy applies to an entire domain, blocking access to a specific wireless network would really only be effective for keeping users from accidentally connecting to other wireless networks that are in close proximity. However, it is important to remember that Group Policies are very flexible. You could therefore create wireless network policies at the OU level so that different policies apply to different computers. By doing so it would be possible to limit wireless network connectivity based on OU membership. By doing so you could limit wireless access by Department for example.
Conclusion
I recommend taking some time to explore all of the different security settings that can be implemented through a wireless network policy. Wireless network policies are very flexible and you can use them to gain a great deal of control over the way in which users connect to wireless networks.
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

