An RODC is a domain controller (DC) that holds a read-only copy of the Active Directory database and the SYSVOL folder. It supports unidirectional replication and only pulls data from its replication partner when the data changes on writable domain controllers. Enterprises can deploy RODCs in branch offices where they cannot guarantee physical security.
RODC characteristics ^
The following characteristics differentiate RODCs from writeable DCs (RWDC).
- Write operations from clients are not possible on an RODC because it holds a read-only copy of the AD database.
- An RODC does not replicate AD and SYSVOL folder data to to RWDCs.
- An RODC holds a complete copy of the AD database, except for credentials and credential-like attributes, called a filtered attributes set (FAS).
- When an RODC receives an authentication request from users from the branch site, it forwards the request to a writeable domain controller. Read more about the authentication process on RODCs here.
- An RODC can cache credentials of least privileged users to provide better authentication performance to branch users. If the RODC has Password Replication Policy enabled and has already cached the credentials, it processes the authentication request locally. Read more about credential caching and FAS here.
- It is possible to delegate rights to standard domain users for RODC administration. Read more about those RODC administration operations here.
Deploying an RODC ^
Prerequisites
Before you deploy an RODC, you need to have at least one writeable domain controller in your environment. In addition, the following conditions are required:
- An administrator account has a strong password.
- The server has a static IP address.
- The server has the latest Windows updates installed.
- The preferred DNS server IPv4 address is configured and points to the writeable DC.
Installing the Active Directory Domain Service
First, you have to install the Active Directory Domain Service (AD DS) feature on your Windows Server 2016 computer. To do so, execute the following PowerShell command and wait for the installation to complete.
|
1
|
Install–WindowsFeature AD–Domain–Services
|
If everything went well, you will end up with the result that the screenshot below displays.
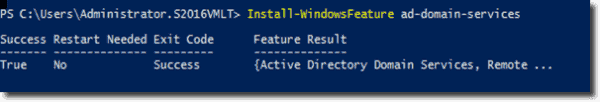
Installing the AD DS role
Promoting a domain member to an RODC
The next step is to promote the server to an RODC with its own DNS server and global catalog by executing the command below. It will prompt you to provide the DSRM (Directory Services Restore Mode) password and credentials that have the permissions to add this DC to the domain.
|
1
|
Install–ADDSDomainController –Credential (Get–Credential) –DomainName <domainName> –InstallDNS:$true –ReadOnlyReplica:$true –SiteName “Default-First-Site-Name” –Force:$true
|
You use the same cmdlet (Install-ADDSDomainController) for deploying a writable DC. The only difference is the ReadOnlyReplica parameter that installs the domain controller as an RODC. If you don’t specify the path to the Active Directory log, the database, and the SYSVOL folder, it will use the default paths.
After executing the command and successfully promoting your server to an RODC, the server will automatically reboot.
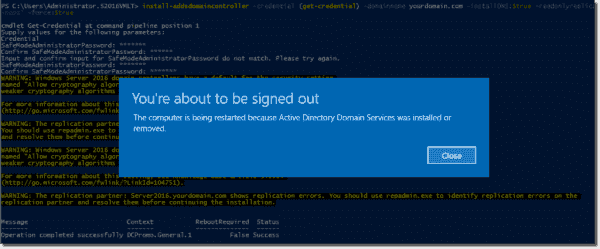
Promoting a server to an RODC
Configuring RODC password caching ^
The new RODC it still using a writeable DC for authenticating branch users and computers. To force the RODC to authenticate users and computer accounts, you have to ensure that the RODC caches the corresponding credentials. For this, you have to configure the Password Replication Policy (PRP) to ensure that it replicates and caches the credentials on the RODC for subsequent authentications.
Allowed and Denied Password Replication Groups
There are two groups in PRP: the Allowed and the Denied Password Replication Groups. The RODC caches account credentials for members of the Allowed Password Replication Group but not those of the Denied Password Replication Group. By default, accounts from privileged groups such as Enterprise, Schema, and Domain Admins are members of the Denied RODC Password Replication Group. To get the complete list, execute the following command:
|
1
|
Get–ADGroupMember –Identity “Denied RODC Password Replication Group” | ft DistinguishedName, Name, ObjectClass
|
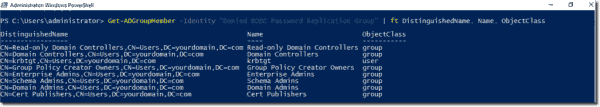
Getting a list of Denied RODC Replication Group members
Adding users accounts to the Allowed Password Replication Group
To add branch user accounts to the Allowed RODC Password Replication Group without the system asking for confirmation, execute the following PowerShell command:
|
1
|
Get–ADUser –SearchBase ‘OU=Students,DC=yourdomain,DC=com’ –Filter * | ForEach–Object {Add–ADGroupMember –Identity ‘Allowed RODC Password Replication Group’ –Members $_ –Confirm:$false }
|
The command fetches all user accounts from the Students organizational unit (OU) and then pipes those accounts to the Add-ADGroupMember cmdlet, which adds them to the group. To confirm that the operation succeeded, run the following command.
|
1
|
Get–ADGroupMember –Identity “Allowed RODC Password Replication Group” | ft DistinguishedName, Name, ObjectClass
|
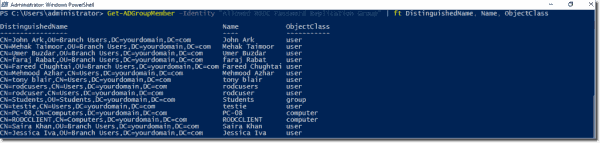
Adding user accounts to the Allowed Password Replication Group
Prepopulating user passwords
If you would like to cache account credentials on the RODC before users log in, you can prepopulate their passwords by executing the following commands:
|
1
2
3
4
|
$users = Get–ADUser –SearchBase “OU=Branch Users,dc=yourdomain,dc=com” ‑Filter *
foreach ($user in $users) {
Get–ADObject –identity $user | Sync–ADObject –Source SERVER2016 ‑Destination SRV–02RODC –PasswordOnly
}
|
Getting an account list of stored RODC passwords
To get the list of accounts with cached passwords on the RODC, execute the following command:
|
1
|
Get–ADDomainControllerPasswordReplicationPolicyUsage –Identity “SRV-02” ‑RevealedAccounts | ft Name,ObjectClass
|
This will return the list of accounts with names and object classes of credentials stored or cached on the RODC with the name “SRV-02.”
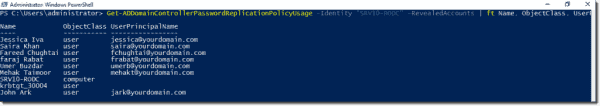
Getting a list of accounts with passwords stored on the RODC
Clearing the RODC password cache
Once an RODC caches passwords, there is no way to delete them on it directly. However, resetting the passwords on a writeable DC also removes them from the password cache on the RODC. The same applies to computers; resetting their accounts removes their credentials from the RODC.
Let’s reset a password of the user with the name “John Ark”:
|
1
|
Set–ADAccountPassword jark –NewPassword (Read–Host –prompt “Provide New Password” –AsSecureString)
|
If you list the accounts with cached passwords using Get-ADDomainControllerPasswordReplicationPolicyUsage, John Ark’s account won’t appear anymore.
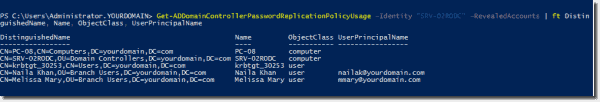
Accounts with cached passwords after resetting the password of a user
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

