A common challenge that integrators run into is managing secrets and subsequently, managing access to secrets. Azure Key Vault is a service that developers can use to store their secrets, keys and other sensitive data. However, there is still a challenge with accessing these secrets. If you are storing the credentials to access Key Vault in a non-secure manner, you have just pushed the problem to another area.
The good news is that we can use a capability called Managed Identities to establish trust between some Azure services. For example, we can have a Logic App that can have a Managed Identity associated with it which can then be added to Azure Key Vault RBAC roles. This establishes trust between our Logic App and Azure Key Vault.
Let’s now explore how we can get this setup.
- Click on Identity as part of your Logic App settings, subsequently turn the Status to On. After this is completed, you will see an Object ID populated which is essentially creating an identity for your Logic App within Azure AD. Copy this value, it will allow us to assign permissions to our Logic App in a subsequent step.
Click on Azure role assignments to continue.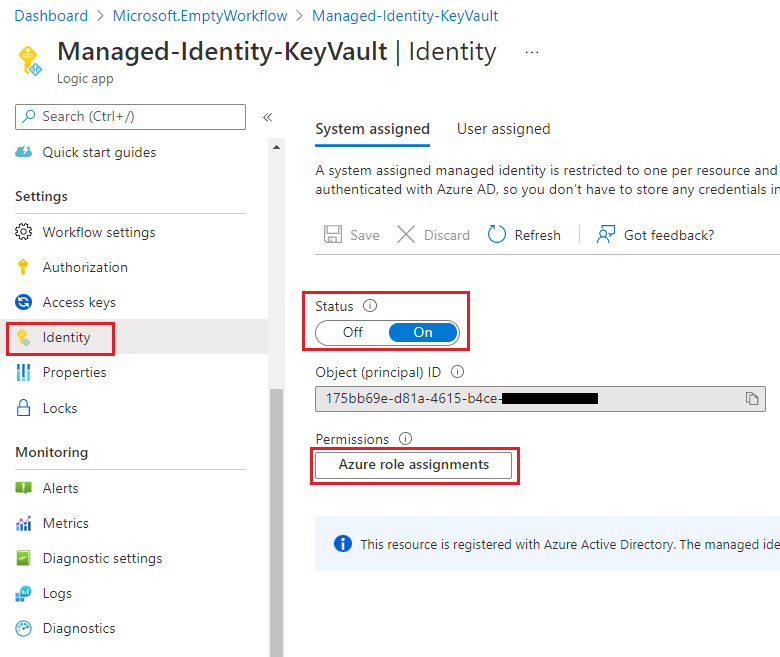
- Click on Add role assignment followed by selecting the appropriate Subscription. From there select the appropriate Scope, Subscription, Resource (your keyvault instance) and the appropriate Role. In this case we will select Key Vault Secrets User which will allow us to extract secrets contents but not modify.
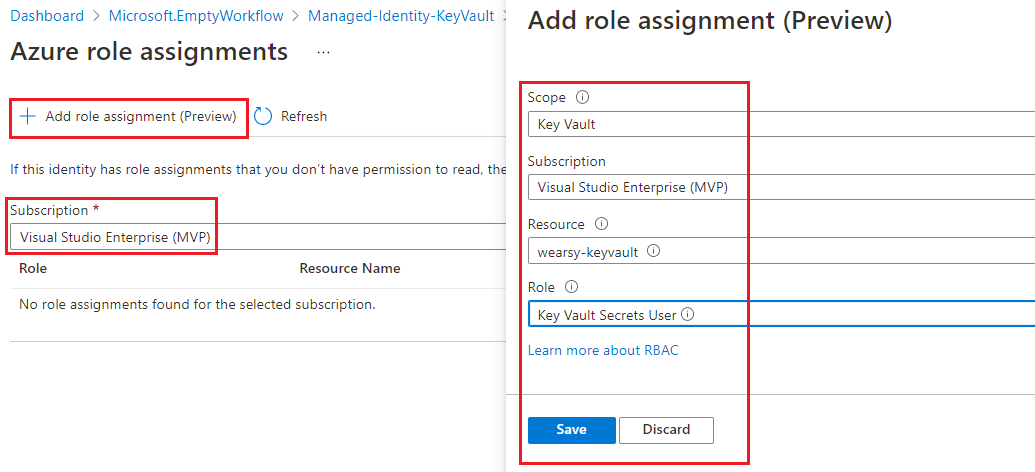
- Repeat this step to include Key Vault Reader
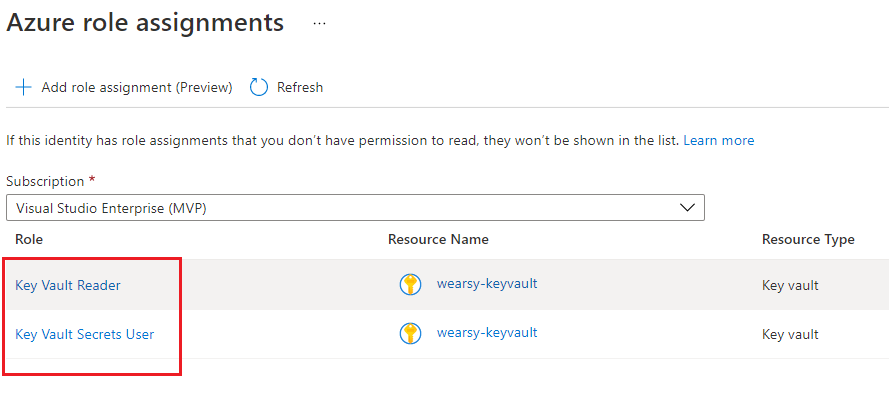
- After we click Save we should see the result.
- Next up, we need to assign an Access Policy on our Key Vault instance and assign access to the Managed Identity that we just created. Find your Key Vault in Azure Portal. Click on Access policies and then Add Access Policy.
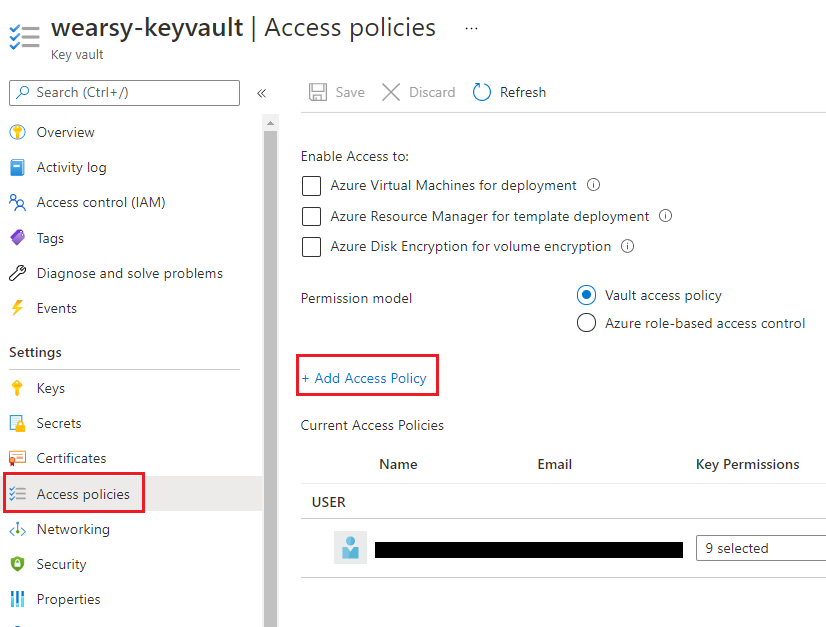
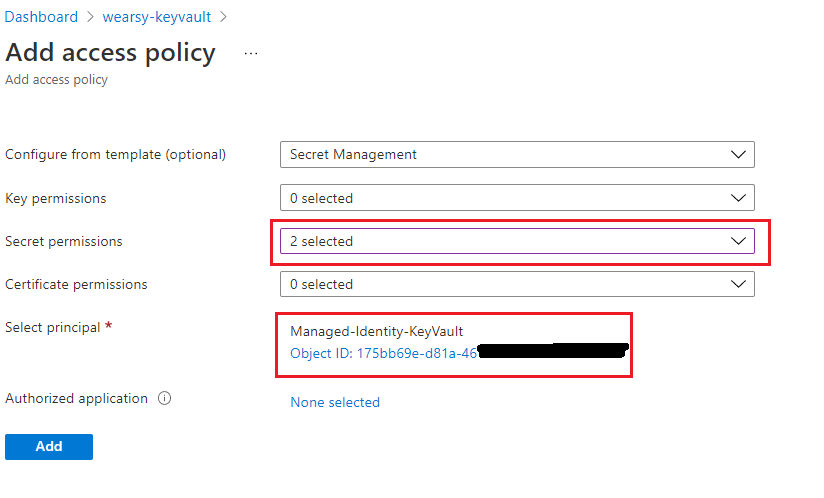
- We can use the Secret Management template to help accelerate completing this task. When it comes to Secret permissions, we will reduce all access to just Get and List. Lastly, we will find our Managed Service principal that we created in step 1. Click Add and Save to continue.
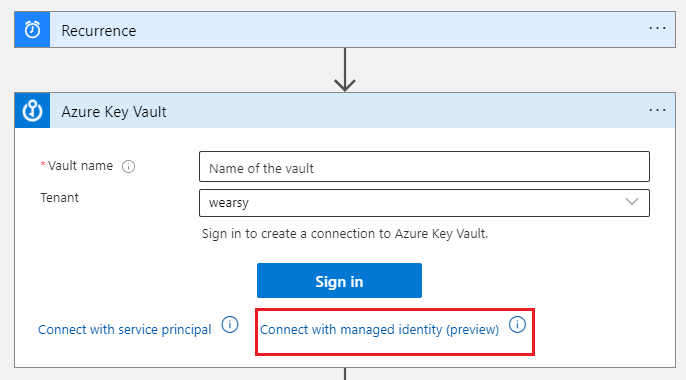
- We can now edit our Logic App and add an Azure Key Vault action to our canvas. Instead of signing in with our credentials, we will click on Connect with managed identity.
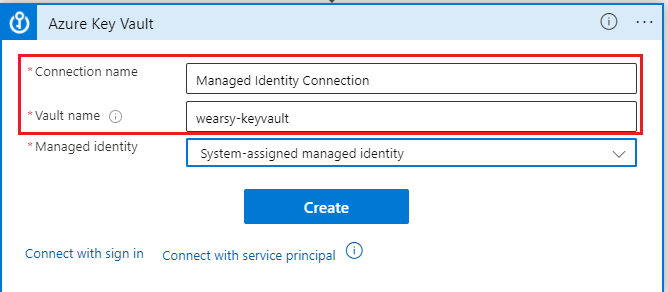
- Specify a Connection name of your choosing and type in the name of your Vault. Click Create to continue.
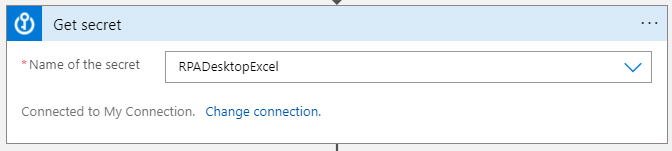
- Select Name of the secret to match the secret that you want to extract.
- We can now add a Compose action where we can write out the Azure Key Vault secret value to ensure our process works.
Note: Whenever using sensitive information in Logic Apps, ensure that you use the Secure Inputs/Outputs feature to avoid secrets leaking into your run history.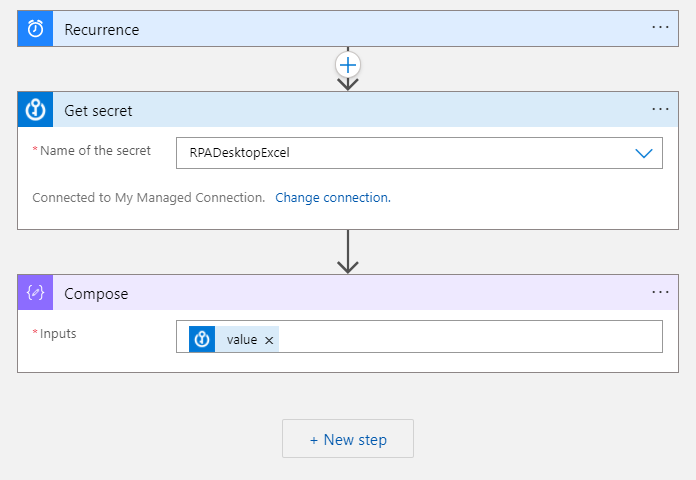
- Test your Logic App to ensure your secret is obtained successfully.
Conclusion
In this post, we discussed how we can use Managed System identities when accessing Azure services like Key Vault. This allows organizations to securely connect to Azure resources without there being a tie to an individual’s credentials/account.
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

