TCP/IP , or Transmission Control protocol/Internet Protocol, is literally the backbone of internet and network communication. The concepts of TCP/IP are difficult to grasp without previous experience, so don’t be dismayed if it doesn’t click instantly. To better help you out, we’ll start from the very beginning- with a definition of just what a network is.
Networks, Protocols, and Suites, Oh Yeah!
A network is simply a collection of computers or similar devices that can communicate over a transmission medium. Don’t worry- that is just a fancy phrase that usually refers to Ethernet cable and other connective wire. You can see a basic network in the diagram below- odds are you’ve already seen something similar.

Simple enough, isn’t it? Just three computers linked together for communication. Sadly, it is a little more complex than that. To actually send any data from one computer to another we need to make use of a network protocol. A network protocol is a set of common rules that defines how data should be sent. These protocols ensure that a message sent from one computer will reach the next, and that it is interpreted correctly. These many different protocols make up TCP/IP, which is referred to as a protocol suite.
But why do we need a special suite? Back when TCP/IP wasn’t around, there were many different proprietary protocols. Since many different companies developed different protocols, many networks just weren’t compatible. Without a common suite like TCP/IP, the internet would not be possible.
A Brief History of TCP/IP
Now that we have a basic understanding of what TCP/IP is for, let’s review how it came to be. Believe it or not, TCP/IP was developed way back in the 1960’s by the United States Department of Defense. Its original designers had a problem- networks at the time were very small and incompatible. Proprietary protocols were in wide use, contributing to the compatibility problem.
In the early days, it was believed that relying on networks could be a disastrous idea. If a particular network node were to be destroyed for any reason, it would likely bring the entire network down. Since a missile or bomb could literally make any point on a network a target, a decentralized system was needed. The goal was to create a network that didn’t depend on other parts of the network to operate- one of the key features of TCP/IP. Review the diagram below for a visual representation of what happens if a computer fails on a centralized network. As you can see, both right and left computers have lost connection to the central computer, since the middle computer is down.
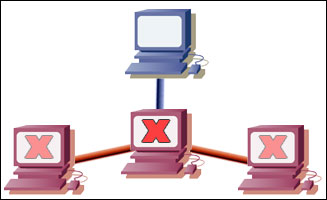
To actually provide a decentralized network, two important features of TCP/IP are used. Instead of one computer having authority over others, computers generally operate as equals. Dynamic routing is another feature that ensures decentralization. If computers are connected through multiple paths, computers will check for alternative routes if one seems to be down. In the above image, we could achieve dynamic routing by connecting both left and right computers to the first centralized computer- this enables us to completely bypass the downed middle computer.
This ambitious project was initially named ARPANET after the Defense Department’s Advanced Research Projects Agency (ARPA). A few years later, research institutions wanted in on the protocol system too. This is the start of what became the foundations of the internet.
Soon after, we had another networking concept arise- the Local Area Network, or LAN. These networks were the solution for offices and institutions to share resources with ease. The first LAN connections were crippled from today’s standards- they lacked internet access. The advent of the gateway enabled protocols to be translated for LAN connections to access the internet- and the popularity of TCP/IP exploded from there.
Key Features of TCP/IP Students and Professionals Should Know
There are many innovative features of TCP/IP, but there are five features in particular that everyone should become familiar with. In no particular order, these features are:
- Application support
- Error and flow control
- Logical Addressing
- Routing
- Name resolution
Application Support
Say you are multitasking- you are uploading files to your website, sending an email, streaming music, and watching video all at the same time. We ran into a critical problem here! How does the computer know where to send each packet of data if multiple applications are running? We sure wouldn’t want to use our email program to watch video, and vice versa!
To combat this problem, we use channels called ports. These numbered ports each correspond to a certain action. Your email, for instance, is likely using port 25 for email operation. Remember the files you were uploading to your website? This kind of data uses the FTP port more often than not, which is usually port 20 and 21. Even browsing a webpage uses a specific port- the HTTP port 80.
In total, there are 65,535 ports for controlling the flow of information. Yikes!
Error and Flow Control
TCP/IP is considered a connection-oriented protocol suite. This means that if data isn’t received correctly, a request to resend the data is made. This is compared to User Datagram Protocol, or UDP, which is connectionless. UDP is a suite of protocols just like TCP/IP, with a few notable differences.
But when wouldn’t you care if data was received correctly or not? UDP is great for broadcasting data- such as streaming radio music. If part of the data was lost, we wouldn’t want to go back and retrieve it! It would waste bandwidth, and would create collisions or noise in our signal. With UDP, the lost data might be represented as a silent spot- which we would take over a noisy retransmission any day!
Logical Addressing
Most computers today come standard with Network Interface Cards, or NICs. These cards are the actual hardware used to communicate to other computers. Each card has a unique physical address that is set at the factory, and can’t be changed. Essentially this is an identifier for the computer it is installed on.
Networks rely on the physical address of a computer for data delivery, but we have a problem. The NIC card is constantly looking for transmissions that are addressed to it- what if the network was very large in size? To put it into perspective, imagine your computer looking at every single bit of data on the internet to see if any of the millions of data packets are addressed to it.
This is where logical addressing comes in. You are probably more familiar with the term IP address, however. These IP addresses can be subnetted on a network to divide a large network into tiny pieces. Instead of looking at every bit of data on the internet, logical addressing allows for computers to just look at data on a home network or subnet.
Routing
A router is a device used to read logical addressing information, and to direct the data to the appropriate destination. Routers are commonly used to separate networks into portions- this greatly reduces network traffic if done correctly.
TCP/IP includes protocols that tell routers how to find a path through the network. This is a vital feature of the TCP/IP suite that enables massive LAN connections to be created.
Name Resolution
And finally, we have name resolution. If you wanted to conduct a search on the internet, you would probably just type Google’s URL into your address bar. What you probably didn’t know is that you aren’t necessarily connecting to “Google.com,” but rather an IP address. Instead of having to remember an IP address, name resolution allows you to remember Google’s name.
It might not be so bad if IP addresses were not so lengthy in size. Which is easier to remember- 64.223.167.147 or Google? This handy service is accomplished on name servers, which are just computers that store tables that translate domain names to and from IP addresses.
Closing Comments
Congratulations, you just got an introduction to the vast TCP/IP world. A lot of technical students tend to skip over the basics. This means you can easily outsmart most of your techie friends with the simplest of questions- just ask them why ARPANET designers pressed for a decentralized protocol suite!
All jokes aside, there is still plenty more to cover. We just got our feet wet with this introduction!
Got a project that needs expert IT support?
From Linux and Microsoft Server to VMware, networking, and more, our team at CR Tech is here to help.
Get personalized support today and ensure your systems are running at peak performance or make sure that your project turns out to be a successful one!
CONTACT US NOW

